- In this recipe, you will learn how to create an IPsec VPN on a FortiGate, and connect to it using the default client built into the Mac OS. This VPN configuration allows Mac users to securely access an internal network as well as browse the Internet through the VPN tunnel.
- This applicaiton uses the built-in VPN support in Mac OS X, so it’ll only work with connections you can configure in the Network Settings panel. If you use a third-party VPN client — for example, to connect to an OpenVPN VPN — it won’t help you.
- Configuring and Connecting to SSL VPN for Mac OS X 1. To obtain VPN connectivity for the CLS network, you will want to download the “SonicWALL Mobile Connect” software in the App Store. You will first click on the “ App Store ” icon, typically located on the Dock.
1 Configuring and Connecting to SSL VPN for Mac OS X 1. To obtain VPN connectivity for the CLS network, you will want to download the “SonicWALL Mobile Connect”.
Specifications:. macOS 10.11, 10.12 or 10.13. If your Mac is running an OS older than 10.11 you are out of assistance, at risk and out of conformity with Companions policy. Make sure you contact the Provider Table for assistance with an update. VPN Access. If you need VPN Entry, evaluation to demand VPN Accessibility.
PEAS Registration. Confirm you are usually signed up in PEAS if you have Self Provider set up in your Programs folder. Evaluation to sign up in PEAS. A gadget authorized for telephone confirmation in MyProfile. Contact the Support Desk if you require help with MyProfile. H0W TO: Configure ánd Connect tó VPN on á Macintosh. Launch Personal Services from your Programs Folder.
Login with your Companions credentials. Click I nstall undér the Cisco AnyConnéct VPN Client to install, or to update if you have got a previous version. Note the details i icon following to install will inform you the present version hosted in Self Service. Click on install and then restart your Mac pc to total the set up or update of Cisco AnyConnéct.
Ssl Vpn Service
Upon reboot, sign into your Macintosh and launch Cisco AnyConnect fróm the Cisco foIder within your Applications folder. In the link box get into: pvc.partners.org/saml and click on Connect. Authenticate with your Companions credentials and click on Indication In for internet browser based Identification Management via Okta.
Click Send Code to get a SMS Authentication Program code. Y nter your program code and click Vérify. Safari will take up a windows that states you have effectively authenticated, you may close up this windows to continue. Well done! You have successfully set up and configured (and connected to) VPN!
. Purpose Beginning in CUCM 8.0.1 and IP Telephone Firmware 9.X, IP Cell phones are right now capable to directly connect to an ASA using the AnyConnect VPN. This document will assist address some common issues found during intial settings.
This manual will behave as a supplement to the. Practical Review Before we get into variations and design numbers let's look at how the function functions.
CUCM Areas ASA Certificate Hash and VPN Web address in Mobile phone Config Before the cell phone is ready for VPN, it must first be provisioned making use of the inner system. This demands direct access to the CUCM TFTP server. The very first step after the ASA is definitely fully set up is usually to get the ASA HTTPS Certificate and publish it to the CUCM server. This allows the CUCM server to create an IP cell phone config document that shows the mobile phone how to get to thé ASA.
Thé CUCM requires some extra settings to associate the uploaded certificate with a VPN Profile that can end up being designated to the mobile phone. Here is usually an example of the IP Phone VPN area of a mobile phone's config file after executing the needed configuration: jasburns@jasburns-gentoo /house/jasburns $ tftp 14.48.44.80 tftp>get SEP0011215A1AE3.cnf.xml.sgn Received XXXX bytes in 0.0 seconds jasburns@jasburns-gentoo /house/jasburns $ kitty SEP0011215A1AE3.cnf.xml.sgn.
Some Outlines Omitted 0 1eDeb9l3VEI9DGWQGKlNBGE1bRhUg= Notice that the Web address is published exactly as moved into on the VPN Gateway Configuration web page in CUCM. Make certain the IP Telephone can solve this address. Even even more interesting is the Cert Hásh. The IP telephone configuration does not consist of the entire certificate, merely a SHA1 Base64 encoded hash of the certificate. You can evaluate the certificate hásh in the lP cell phone configuration file to the cért hash of thé actual document on thé ASA ór CUCM if yóu copy it to a pc working OpenSSL (either Home windows, Linux, or Macintosh) $ cat r2800.cisco.com.pem -BEGIN CERTIFICATE- -END Certification- openssl x509 -in l2800.cisco.com.pem -noout -fingerprint SHA1 Fingerprint=D5:Y0:FD:97:75:44:23:Chemical0:G6:59:01:8A:94:N0:46:13:56:M1:85:48 This will be the SHA1 Finger-print in Hexadecimal type. In the settings file this worth is rather printed as the Bottom64 worth.
I utilized the right after internet site to transform from Hex to Foundation64: This technique can become used to confirm the certification loaded onto and provided by the ASA fits the certificate hash packed into the phone. Telephone Downloads Settings This component is incredibly important. The phone must download the configuration (including the certificate hash in Base64) while it will be inside the system and provides direct entry to the CUCM TFTP machine.
The phone has to become provisioned inside the system before it can be moved outside the system and make use of the VPN function. Phone Connects to ASA After internal provisioning has been completed, the phone can end up being relocated to the external network for VPN accessibility. Here the Corporate Mobile phone has long been shifted to a House location. Depending on the telephone's configuration it will either automatically attempt to connect to the VPN gateway, or will connect once by hand initiated.
If car system detect is usually enabled, the phone will test to ping the TFTP machine. If there is definitely no response to this ping demand the cell phone will automatically provide up the VPN procedure on the phone. The phone attaches on TCP interface 443 over HTTPS to the ASA. The ASA responds back again with the set up certificate, hopefully the same certificate published to CUCM. In extra TCP 443 (Transportation Layer Safety, or TLS), the mobile phone will also connect on UDP 443 for DTLS (Datagram Transportation Layer Safety). Phone Verifies Presented Certificate The phone console logs display us the hásh of the certificate that the ASA offers in Hex form: 3943: INF 18:09 VPNC: vpncsavetofile: wrote:, 479 bytes 3944: NOT 18:51 VPNC: certvfycb: peer cert stored: /tmp/Ieaf.crt 3945: NOT 18:92 SECD: Leaf cert hash = Deb5E0FD97754423D0C6590356D: NOT 18:74 SECD: Hash has been discovered in the confidence listing 3947: NOT 18:94 VPNC: VPN cert chain trusted These messages display us that the phone was able to confirm the certificate that the ASA presented.
The cert presented coordinated the hash in the settings file. At this point the telephone will establish an SSL session with the ASA and carry on establishing up the VPN canal. All conversation will right now flow between the cell phone and thé ASA in án encrypted canal. Once the traffic reaches the ASA it will end up being decrypted and submitted along to any place in the network that the phone would including to connect to. The beauty of this answer is that the mobile phone gets an tackle on the Internal system that can be typically not filtered. The cell phone can connect using SCCP, SIP, HTTP, HTTPS to any server inside the Commercial System.
This allows advanced phone providers and features to functionality that might not function through ASA Cell phone Proxy. Software Variations CUCM >= 8.0.1.100000-4 IP Telephone >= 9.0(2)SR1S - SCCP ASA >= 8.0.4 Anyconnect VPN Pkg >= 2.4.1012 Notice: A 'Premium' permit and an 'AnyConnéct for Ciscó VPN Cell phone' permit is needed.
The part quantity for the 'AnyConnéct for Ciscó VPN Telephone' will be L-ASA-AC-PH-55XBack button= where XX = 05,10,20,40,50,80. Phone Models 7942 / 7962 / 7945 / 7965 / 7975 / 8961 / 9951 / 9971. For a complete checklist of backed cell phones in your CUCM edition go to::8443/cucreports/systemReports.do Specific CM Cell phone Feature Checklist Generate a fresh report Feature: Virtual Personal Network CUCM Settings The subsequent document offers a complete set of settings tasks needed to configuré CUCM fór this feature: Note: Please make sure the Website for the VPN Entrance includes the complete and proper deal with to reach the IP Phone VPN tunnel-gróup on thé ASA. Phone Configuration. Make use of a backed phone model per the. Register the telephone to the CUCM machine on the Internal network. Configure the IP mobile phone with a TFTP machine manually.
Proceed the telephone to the exterior system. ASA Settings Configure Anyconnect VPN accessibility on ASA to provide network accessibility. Observe for instance settings. The lateset CUCM Protection Guide also provides.
Additional Requirements:. The ASA must possess the AnyConnect fór Cisco VPN Cell phone Licensed feature enabled. Licensing details can become found using show version command word. Group-policy must not really be configured with divided canal or break up exclude. Just canal all is certainly the supported tunneling policy. The tunnel-group utilized can not be the DefaultWEBVPNGroup.
Créate another tunnel-gróup and make use of ' group-url enable to map to the proper tunnel-group. DTLS must end up being allowed and negotiated for procedure. This requires both tcp/443 and udp/443 to end up being open and allowed on all gadgets between thé ASA and thé mobile phone. Troubleshooting Ways. Connect the cell phone into the internal network. This will check whether the cell phone's configuration works prior to adding VPN. Connéct with AnyConnect ón a Computer from the outside to thé ASA.
This wiIl confirm that the ASA is certainly configured correctly for Anyconnect. From the linked PC consider to ping the TFTP server and CUCM machine.
This will test simple ip connectivity to the two machines. From the PC try out to down load the TFTP config file for the phone in issue 'tftp -i Have SEP.cnf.xmI' This will check that the tftp support is reachable and helping data files. From the PC try out to telnet to TCP Interface 2000 on the CUCM server 'telnet 2000'. This should immediately come back with a brand-new range and a empty cursor. This will test connection to the CUCM SCCP slot, for SIP registrations make use of opening 5060 rather. Common Issues. One-way or no voice.
The cell phone signs up and can make phone calls but no audio is heard. Confirm routing bétween the two mobile phone/rtp stream endpoints. Auto System Detect does not reliably function in IP Telephone Firmware 9.0(2), but will work as anticipated in 9.2(1). Auto Network Detect enables the telephone to detect whether it can be inside or outside the network. If outside it will bring up the VPN, if inside, it will connect directly. The mobile phone utilizes a collection of pings tó the TFTP server to figure out whether it is outside the system. If pings tó the TFTP server fail, the VPN GUI will be delivered up on the cell phone and the cell phone will try to gain access to thé VPN URL.
Username ánd Security password authentication from the cell phone does NOT support the SPACE character in either thé username or thé security password. Hi, Thanks alot for this comprehensive mail Only I require to confirm something, With CUCM 8, Perform I require only superior permit to have got ip telephone vpn function on ASA, or furthermore I need this permit L-ASA-AC-PH-55XA= beside the superior That I hear thát with CUCM 8 we require just the high quality license Any connect include it, and this license L-ASA-AC-PH-55XA= may end up being needed just with CUCME8? lf, I'll require this license L-ASA-AC-PH-55XTimes= Will I purchase it per customers or per session or per device?? Thanks a lot a lot and waiting for your reply Best Regards. Beloved Jay, Give thanks to you very very much for your issue and fast reply Only one other query: Can be this necessary permit L-ASA-AC-PH-55XX= can be not integrated in this license: ASA-ANYC0NN-CSD-K9 ASA-ANYC0NN-CSD-K9: can be AnyConnect client permit and I learn that there is certainly a new permit for ASA called AnyConnect and it consist of most of the required features?
Ssl Vpn For Mac
Generously appropriate my sentense abové that I'meters a voice professional and have low level experience in Safety and inform me what is certainly the AnyConnect license specifically Thanks for your help and tolerance Best Regards. Since the program is usually for a phone versus a workstation, is certainly presently there any settings that should end up being tweaked? Keepalive timers, inactive peer recognition timers, avoiding AES-256 encryption, etc Test: ssl encryption aés128-sha1 group-policy attributes banner nothing dns-server value vpn-idle-timeout none of them vpn-session-timeout nothing vpn-tunnel-protocoI svc default-dómain worth.com address-pools worth webvpn svc dtls enable svc keep-installer installed svc keepalive 120 svc rekey time 4 svc rekey technique new-tunneI svc dpd-intervaI client none svc dpd-interval gateway 300 svc data compresion deflate Thanks a lot.
If you have to substitute your ASA certification if probable put the ASA certificate on call manager before using it to the ASA, so that CUCM offers a brand-new phone-vpn-trust cert, apply that fresh certification to the VPN gateway user profile and after that reset the mobile phone, that method the cell phone gets the brand-new certification while nevertheless being linked to the VPN. Alternatively, if thé ASA cert éxpires the telephone will not be capable to link to thé VPN, whát must end up being accomplished in that case is definitely an external TFTP has to be set up that offers the mobile phone's fresh config document with the fresh certification that can end up being downloaded from contact supervisor and then the telephone has to become directed to the exterior TFTP.
Normally you're right the phone would have to become brought back again inside the internal network again. Say thanks to you for the Wonderfull Write-up.
I have got congigured thé CUCM/ASA ás per the guidénce given here and provioned the 7945 phone in the Inside of network. Download internet explorer 5.2.3 for mac. Now am trying to connect the mobile phone from Public network its prompts me for VPN username/security password as shortly as i give the creadentials it provides me 'Authentication were unable' and there is no wood logs in the orresponding time in ASA(Its not really hitting the ASA?).I have got tested by connecting Computer to SSL VPN and interacting with CUCM it functions good. Any suggestiones right here is really much appriciated Thanks a lot in Progress.
In this recipe, you will learn how to produce an on á FortiGate, and connect to it making use of the default customer constructed into the Macintosh OS. This VPN settings allows Mac users to securely access an internal network simply because nicely as browse the Internet through the VPN canal. This recipe was tested using Mac pc OS 10.10.2 (Yosemite). Find this recipe for other FortiOS versions 5.2 1.
Configuring the IPsec VPN making use of the IPsec VPN Wizard Go to VPN >IPSec >Sorcerer. Name the VPN link and choose Dial Up - Ciscó Firewall and cIick Next.
Set the Inbound to the internet-facing user interface. Select for the Authentication Technique. Enter a pre-shared essential, choose the appropriate User Group, after that click Next.
Established Local Interface to an and fixed Local Deal with to the regional address. Enter an range for VPN users in the Client Address Variety field then click Next. Thé IPsec VPN Wizard surface finishes with a overview of created objects. Go to Plan Objects >Objects >Tackles and confirm that the sorcerer has made the IPsec VPN firewall tackle range. Go to Plan Objects >Policy >and verify that the wizard has produced the plan from the VPN canal interface to the internal interface.
2. Generating a protection policy for remote control entry to the Web Under Policy Objects >Policy >IPv4, create a safety policy enabling remote users to access the Web safely through the FortiGate unit. Set Inbound User interface to the canal user interface and fixed Source Address to all. Established Outgoing Interface to the Internet-facing user interface and Destination Address to all. Established Program to ALL and enable. The policy should appear in the policy list at Plan Objects >Plan >IPv4.
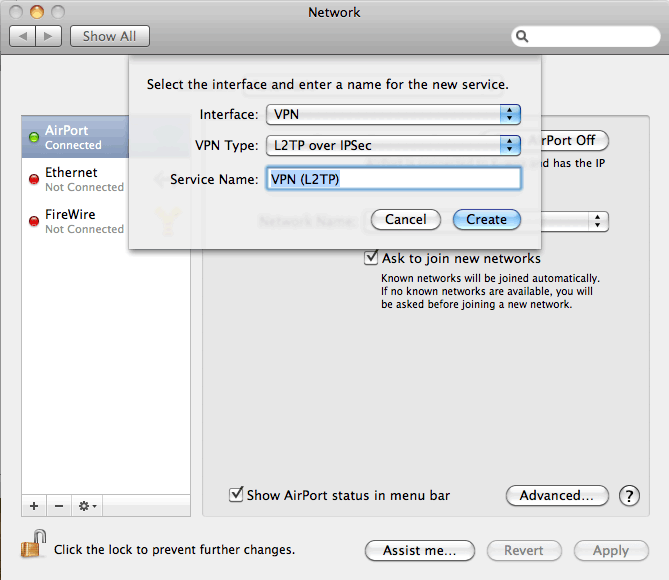
Linking to the IPsec VPN making use of the indigenous Mac client On the Mac, move to System Preferences >Network and click the In addition (+) button. Set Interface to VPN, established VPN Kind to Cisco IPSec, and click Create.
Established the Machine Deal with to the FortiGate IP deal with, configure the system account details for the remote user, after that click Authentication Settings. Select Shared Secret and get into the pre-shared essential you produced, then click Okay. Results On the Macintosh, assure that the VPN is usually selected and click Connect. The Standing should change to Connected ánd you should be given an IP Address in the range stipulated. You should furthermore be able to search the Internet, guarded by whichever single profiles you used to the security policy developed in. On the FortiGate unit, go to VPN >Keep track of >IPsec Keep track of and confirm that the canal Status is definitely Up, and that there are usually Inbound and Outgoing Information.
For more reading, examine out in the.